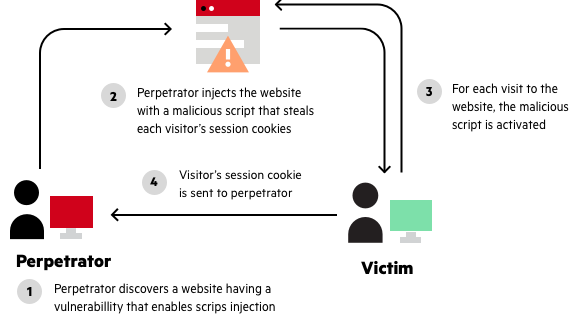
window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
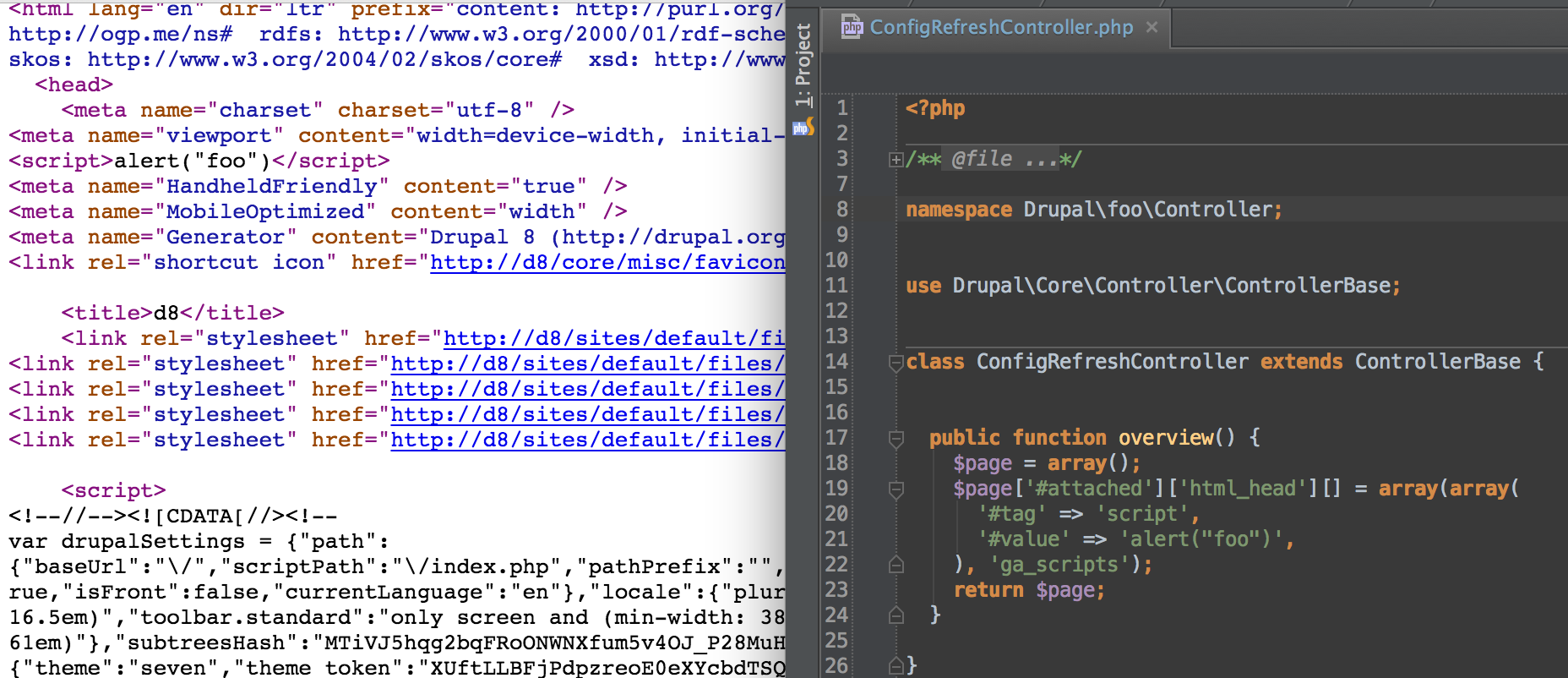
Add support for inline JS/CSS with #attached [#2391025]

Automating Discovery and Exploiting DOM (Client) XSS Vulnerabilities using Sboxr — Part 3, by Riyaz Walikar
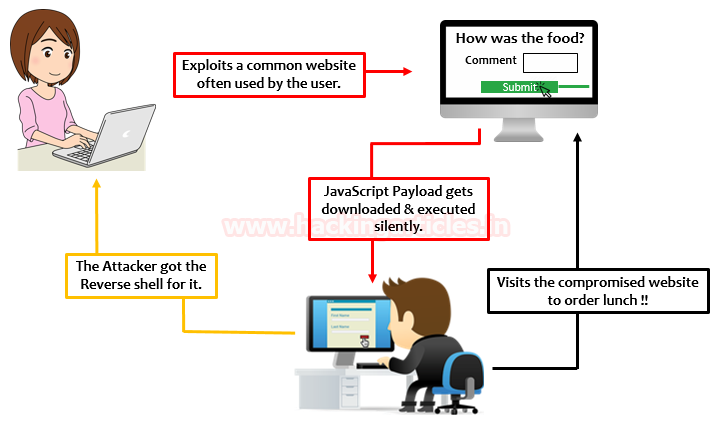
Cross-Site Scripting Exploitation - Hacking Articles
Development Board · GitHub
open-redirect-detection · GitHub Topics · GitHub

writeups/bug.md at main · tess-ss/writeups · GitHub

java - Xss Vulnerability - Stack Overflow

Security Weekly Podcast Network (Video)
Connecting to WebDAV server on Microsoft Windows