Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Descrição
Describing activities of a crime group attacking Ukraine.

Initial Access Brokers Fueling Ransomware

Initial access brokers: How are IABs related to the rise in ransomware attacks?
Information March 2023 - Browse Articles

A survey on recent optimal techniques for securing unmanned aerial vehicles applications - Syed - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

US6968571B2 - Secure customer interface for web based data management - Google Patents

Hacking Archives - Page 7 of 15 - HaXeZ

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
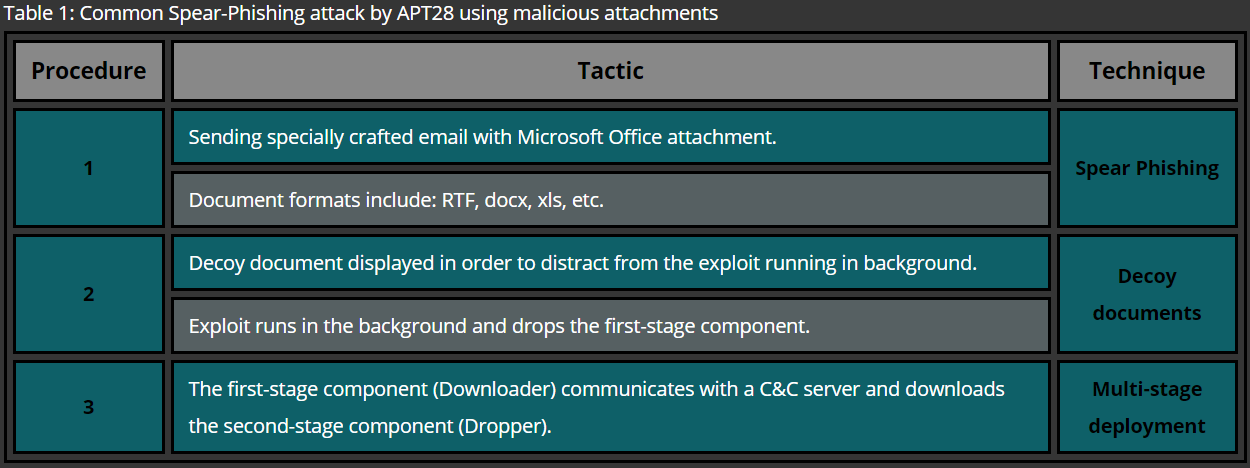
Initial Compromise