Lone-Actor Terrorism: Policy Paper 2: Attack Methodology and Logistics
Por um escritor misterioso
Descrição

Wiki-Slack attack allows redirecting business professionals to malicious websites

How Afghanistan's Overthrown Governing Elites Viewed the Violent Extremism Challenge – Combating Terrorism Center at West Point
tm239600-23_424b4alt - none - 24.7188496s

HIGH-RISK SERIES Efforts Made to Achieve Progress Need to Be Maintained and Expanded to Fully Address All Areas

PDF) Countering Lone-Actor Terrorism Series No. 2 Lone-Actor Terrorism Definitional Workshop

Cyber Defense eMagazine July Edition for 2022

EvilProxy used in massive cloud account takeover scheme

9 ~,~i - National Criminal Justice Reference Service

The War Against the Terror Masters
Trust and suspicion - Morton Deutsch, 1958

Institute for Security and TechnologyBlueprint for Ransomware Defense: An Action Plan for Ransomware Mitigation, Response, and Recovery for Small- and Medium-Sized Enterprises - Institute for Security and Technology

HTML Smuggling technique used in phishing and malspam campaigns
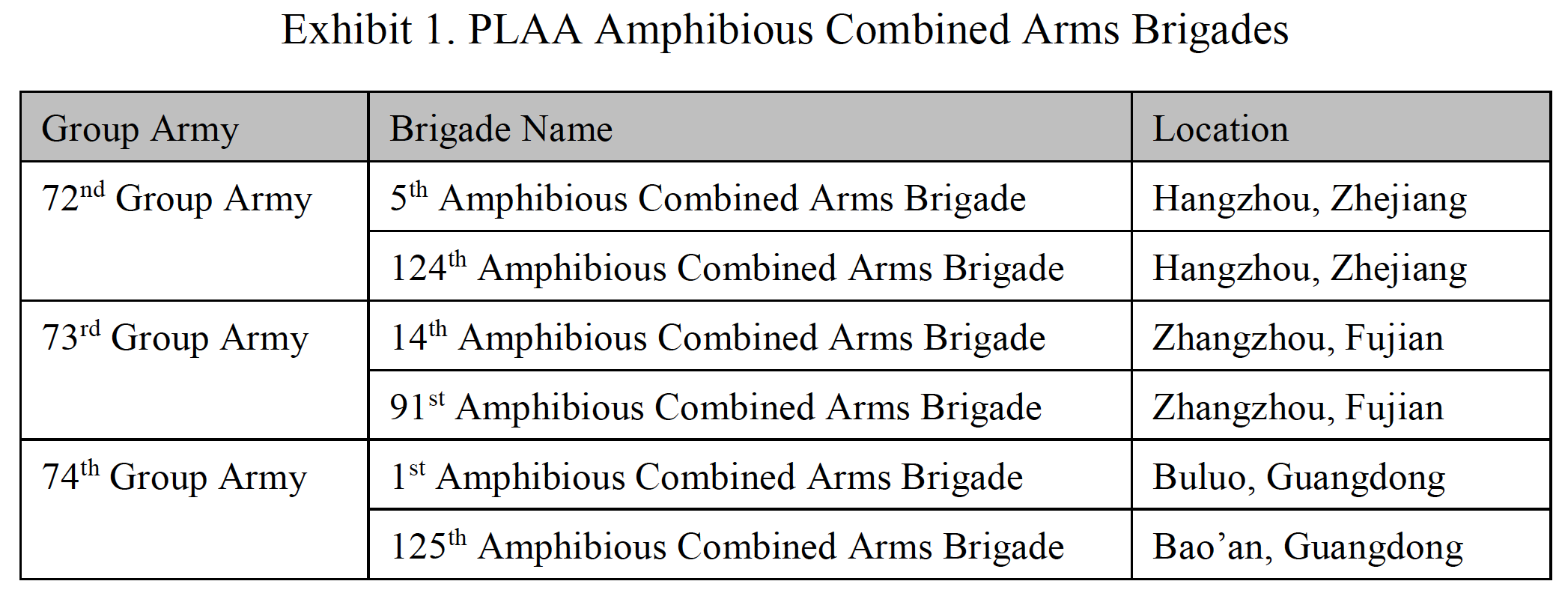
CMSI China Maritime Report #20: “The PLA Army Amphibious Force: Missions, Organization, Capabilities, and Training”

Distinguishing lone from group actor terrorists: A comparison of attitudes, ideologies, motivations, and risks - Dhumad - 2023 - Journal of Forensic Sciences - Wiley Online Library







