Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Descrição
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..
How Cybercriminals Abuse OpenBullet for Credential Stuffing
Captcha Solver: Auto Recognition and Bypass
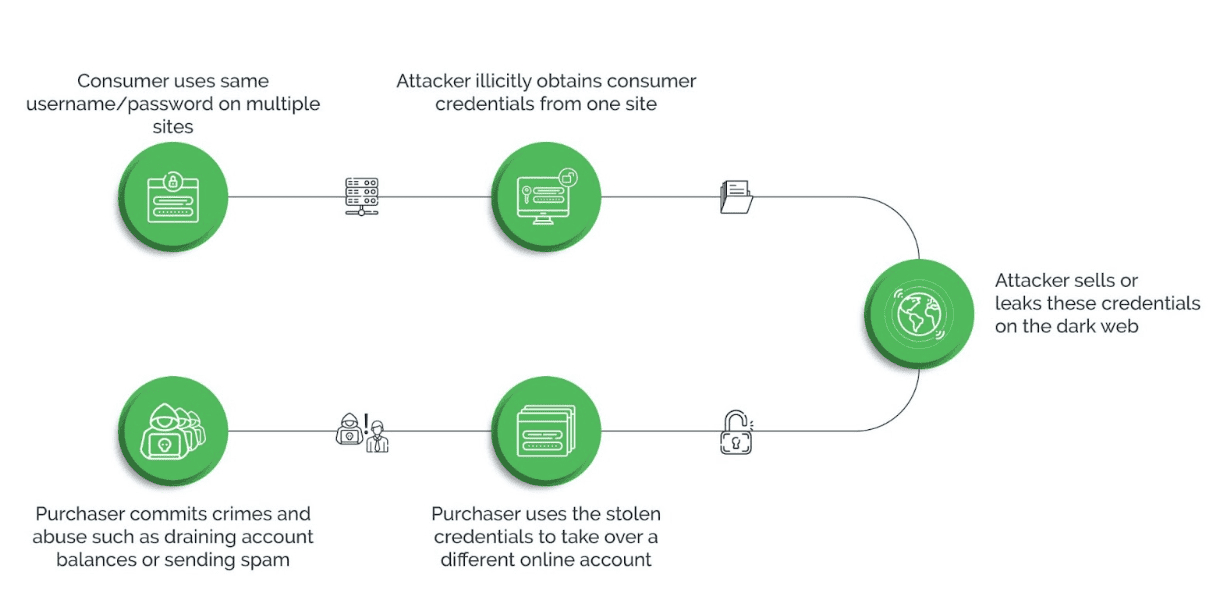
What Is Credential Stuffing?
How to Prevent Credential Stuffing
The Economy of Credential Stuffing Attacks

What Is Credential Stuffing?

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools

An easy guide to Credential Stuffing Attacks - How businesses can Detect and Prevent it? - Payatu
The Ultimate Guide to Avoiding CAPTCHAs in Web Scraping

10 Tips To Stop Credential Stuffing Attacks, by Jarrod Overson
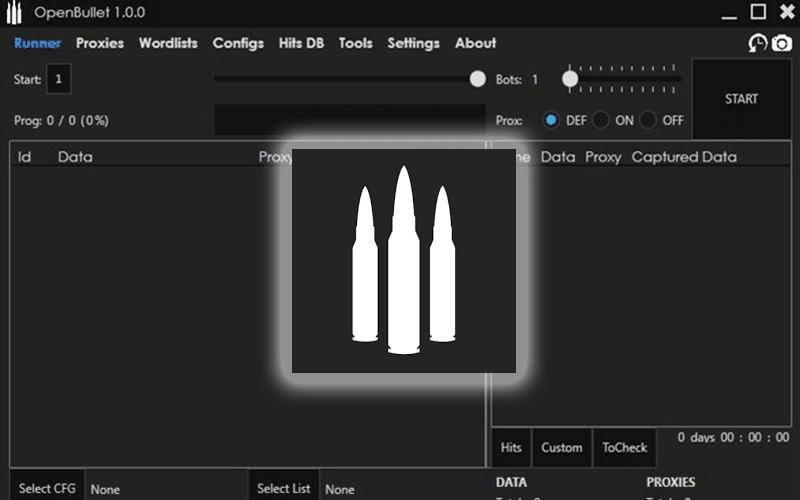
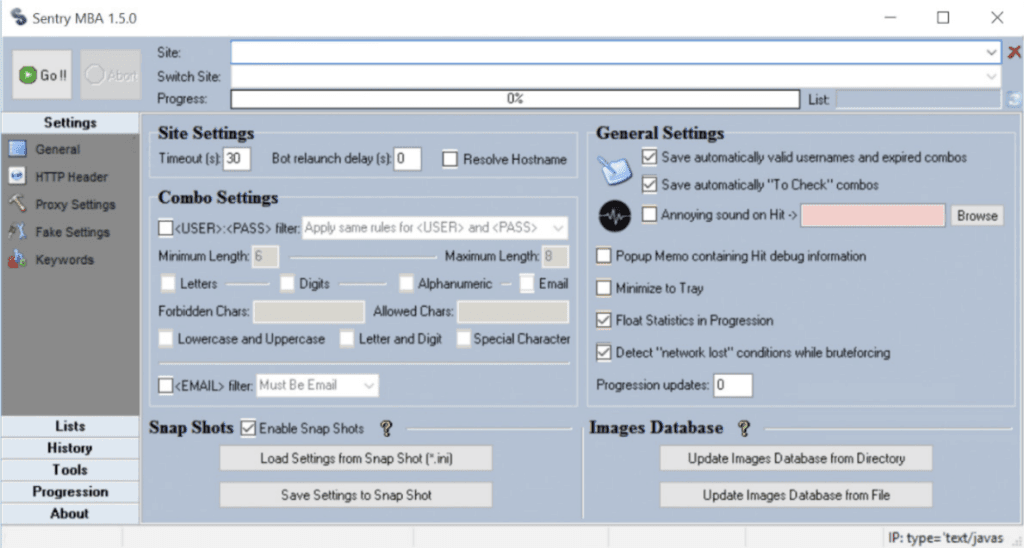
Cracking Tools that Automate Credential Stuffing & ATO