Malware analysis Malicious activity
Por um escritor misterioso
Descrição
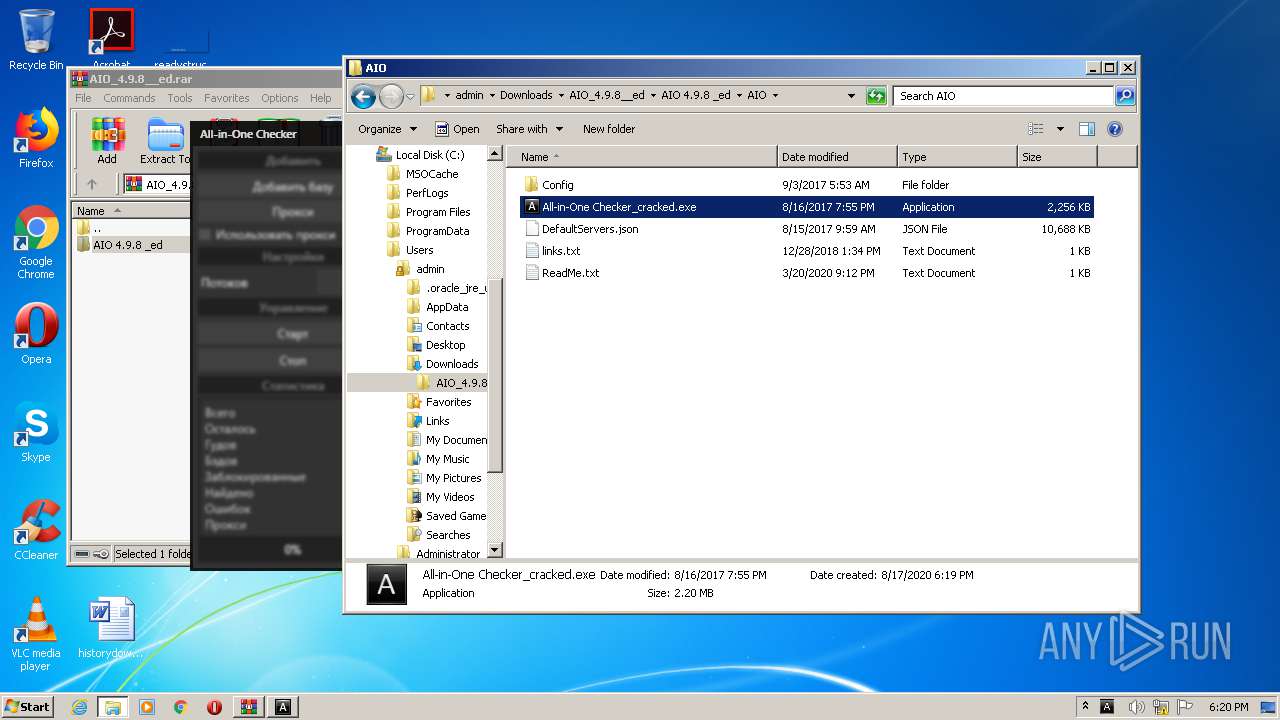
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Malware Analysis Benefits Incident Response

Malware Analysis: Steps & Examples - CrowdStrike

Top 10 Types of Information Security Threats for IT Teams

Malware leveraging public infrastructure like GitHub on the rise - Security Boulevard

Comprehensive Protection Strategies Against Cyber Threats
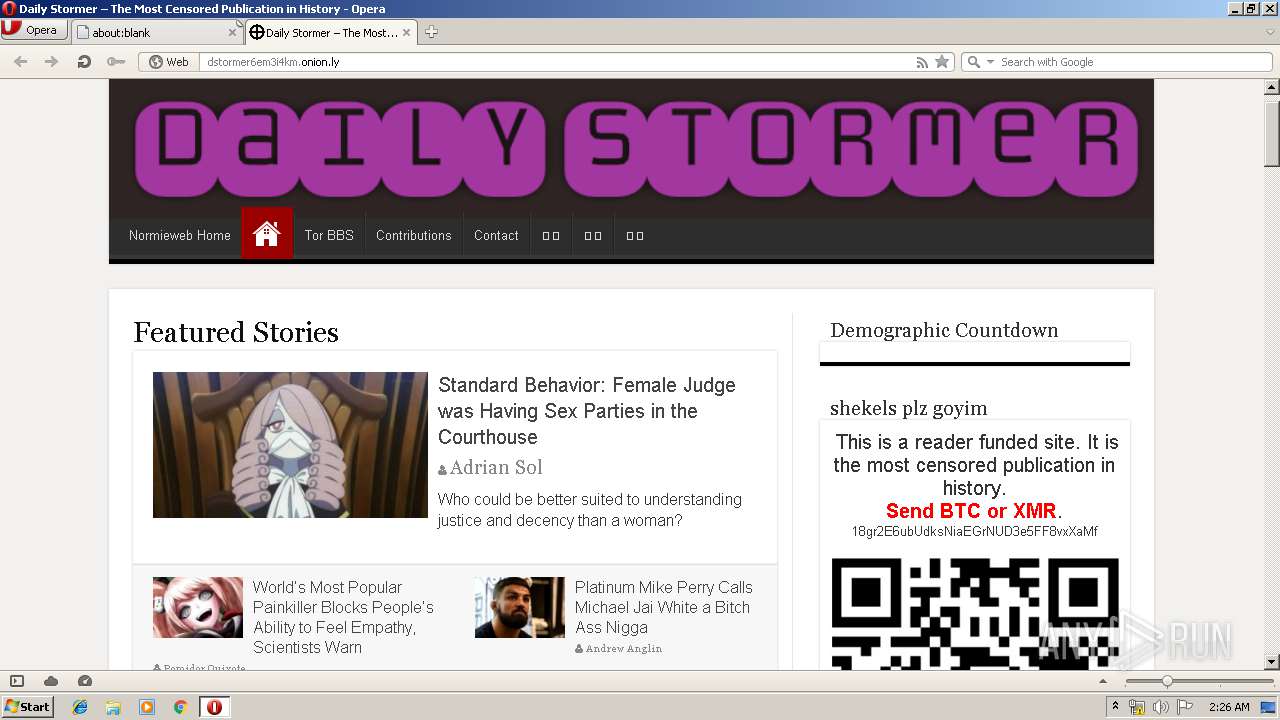
Malware analysis Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

What is Malware? Definition, Types, Prevention - TechTarget

Endpoint Detection and Response, Free - What is EDR Security?
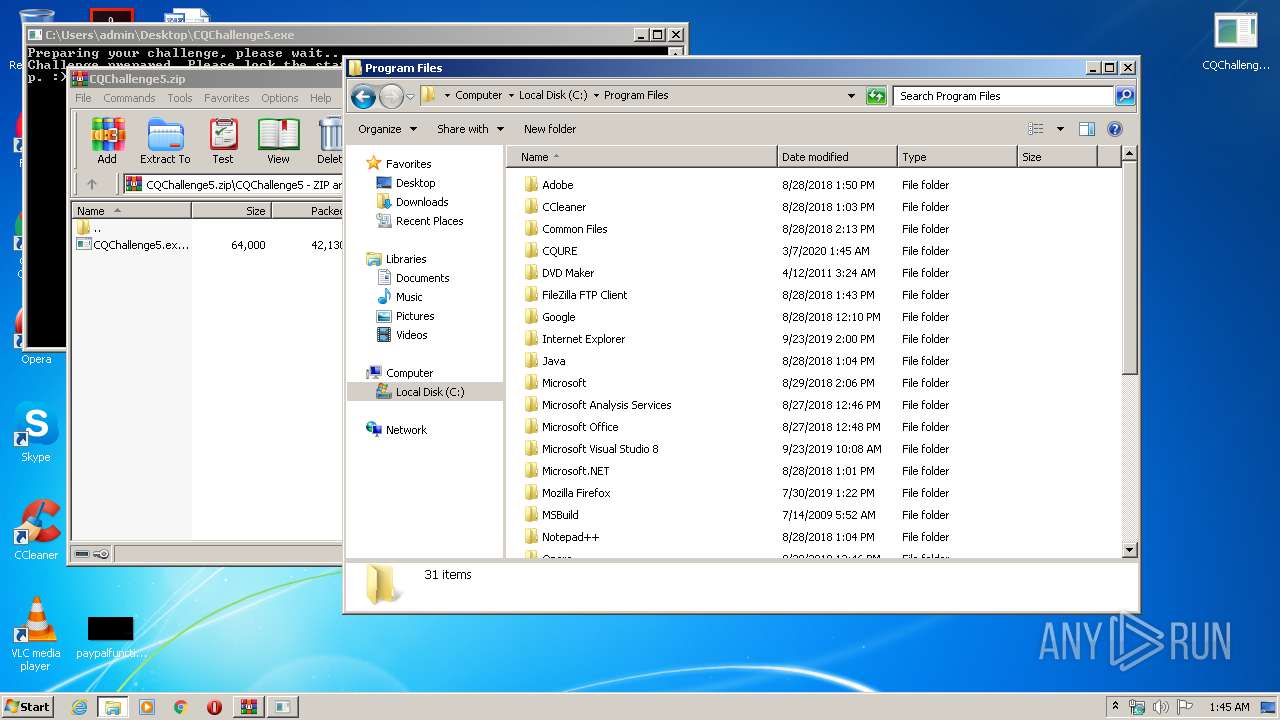
Malware analysis CQChallenge5.zip Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog