Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Detail procedure of malware analysis
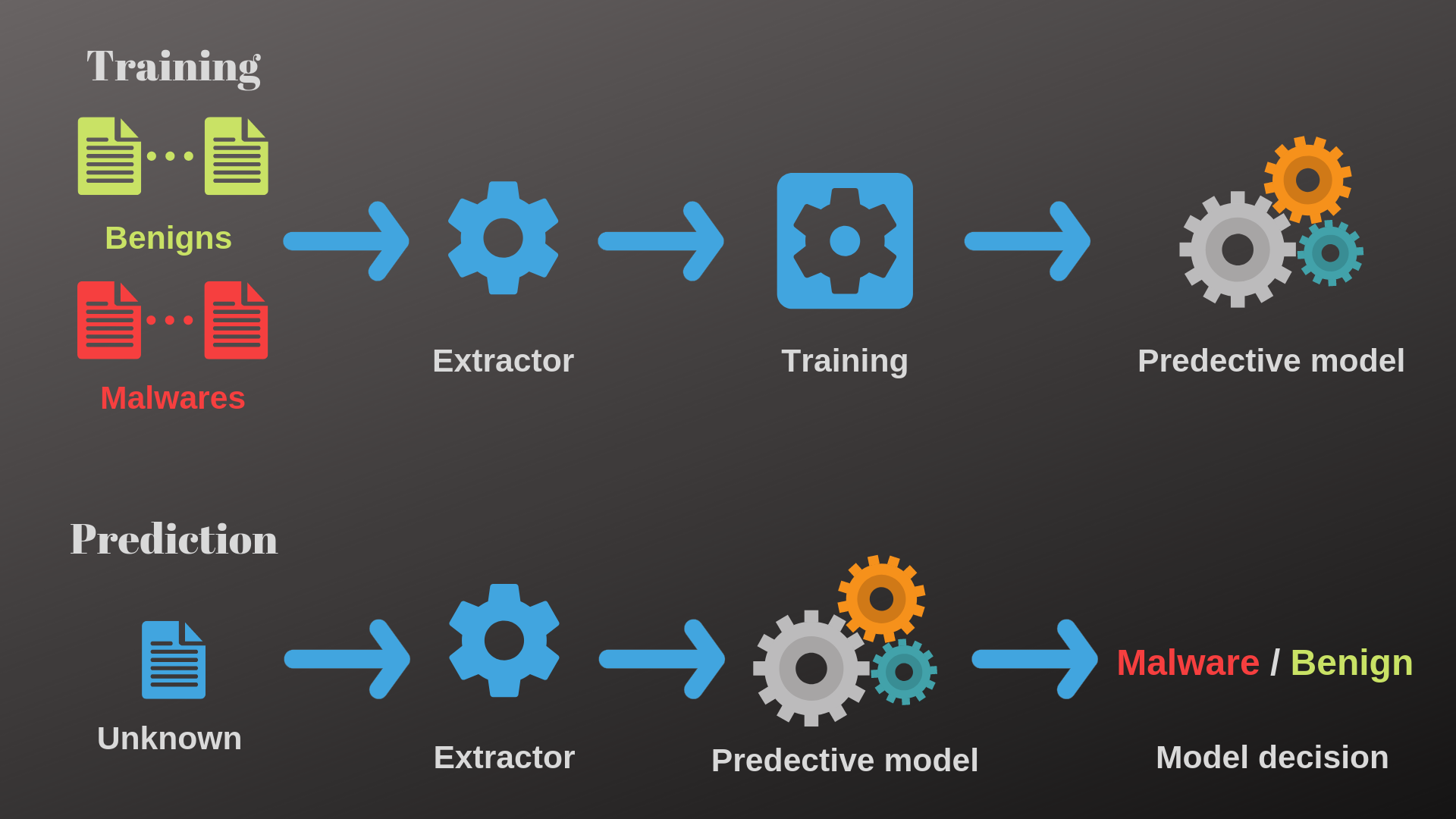
Feature Extraction and Detection of Malwares Using Machine Learning

How to Analyze Malware's Network Traffic in A Sandbox

Malware analysis metasploit.bat Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

How to Do Malware Analysis?

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Rising threats: Cybercriminals unleash 411,000 malicious files daily in 2023
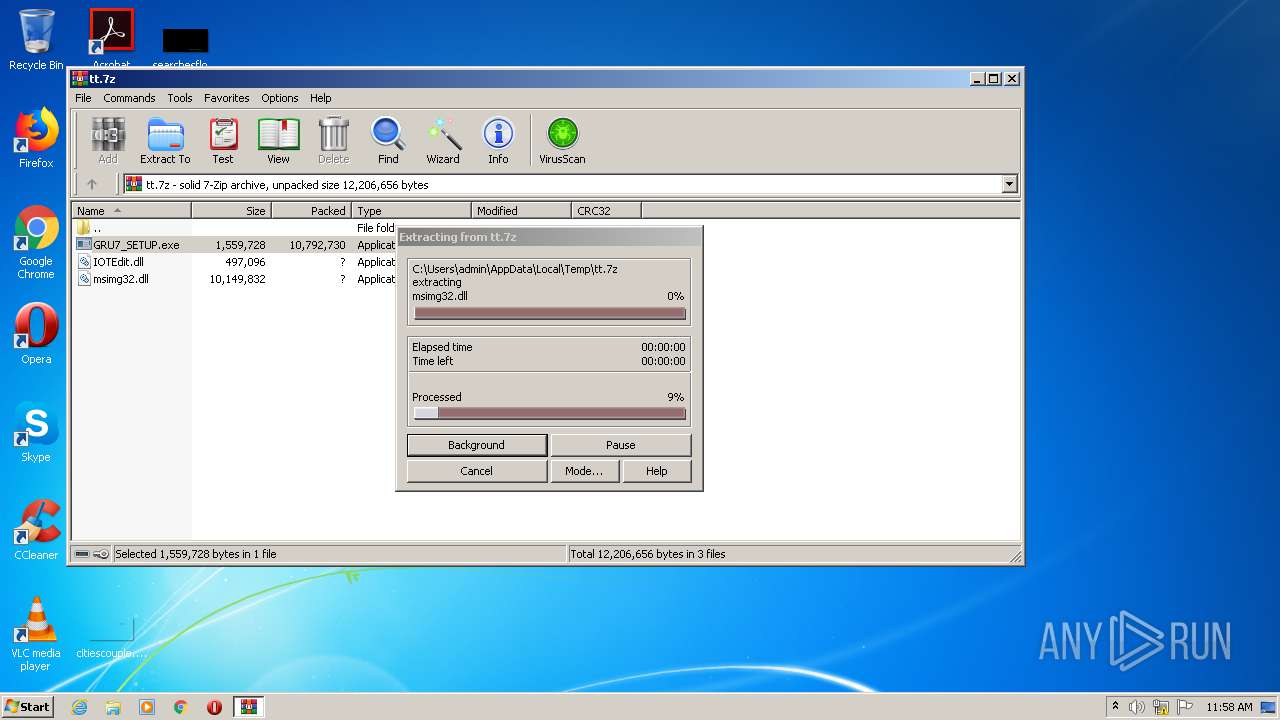
Malware analysis tt.7z Malicious activity

Cybersecurity Search Engine
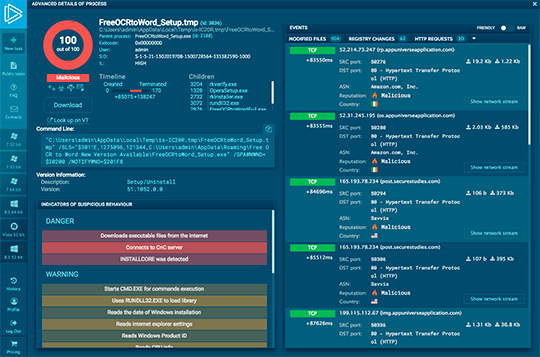
Interactive Online Malware Sandbox

Malware analysis Program_Install_and_Uninstall Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike