Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Brute Force Attacks: Password Protection

StopRansomware: Rhysida Ransomware

What to Include in a Malware Analysis Report

Malware Analysis: Steps & Examples - CrowdStrike

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
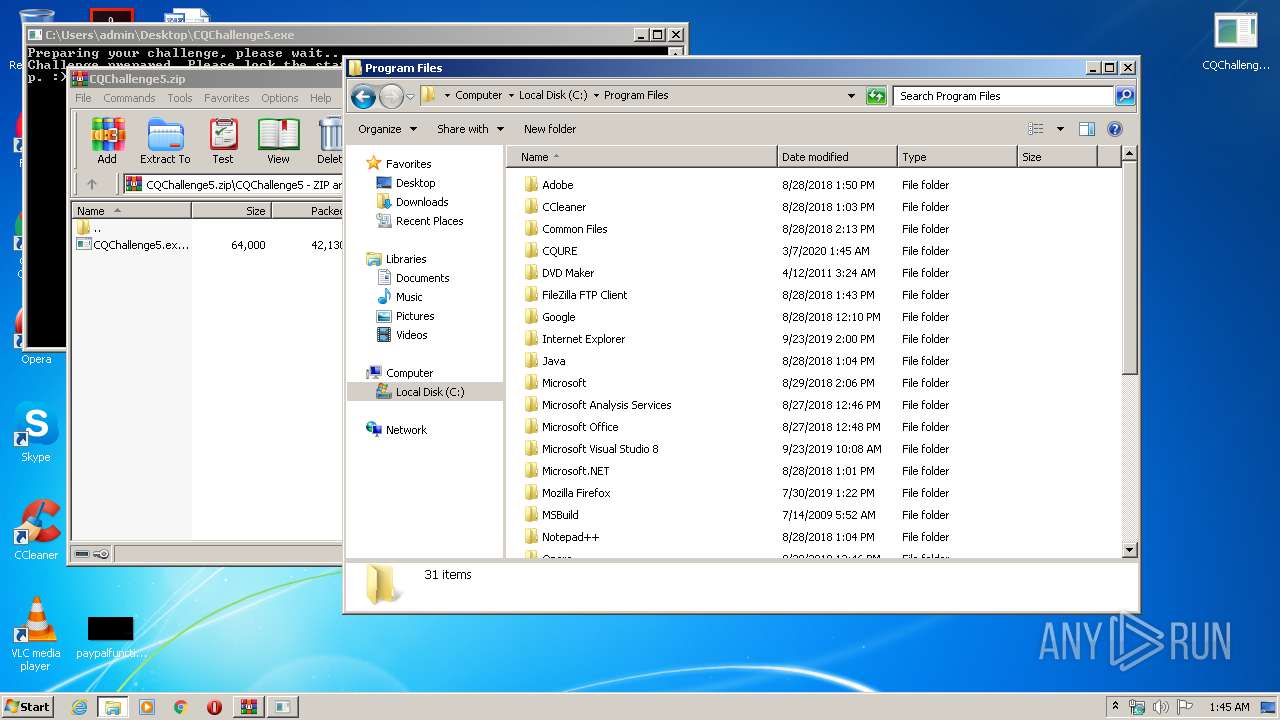
Malware analysis CQChallenge5.zip Malicious activity

TryHackMe Hacktivities

What is Malware? Definition, Types, Prevention - TechTarget

Detail procedure of malware analysis
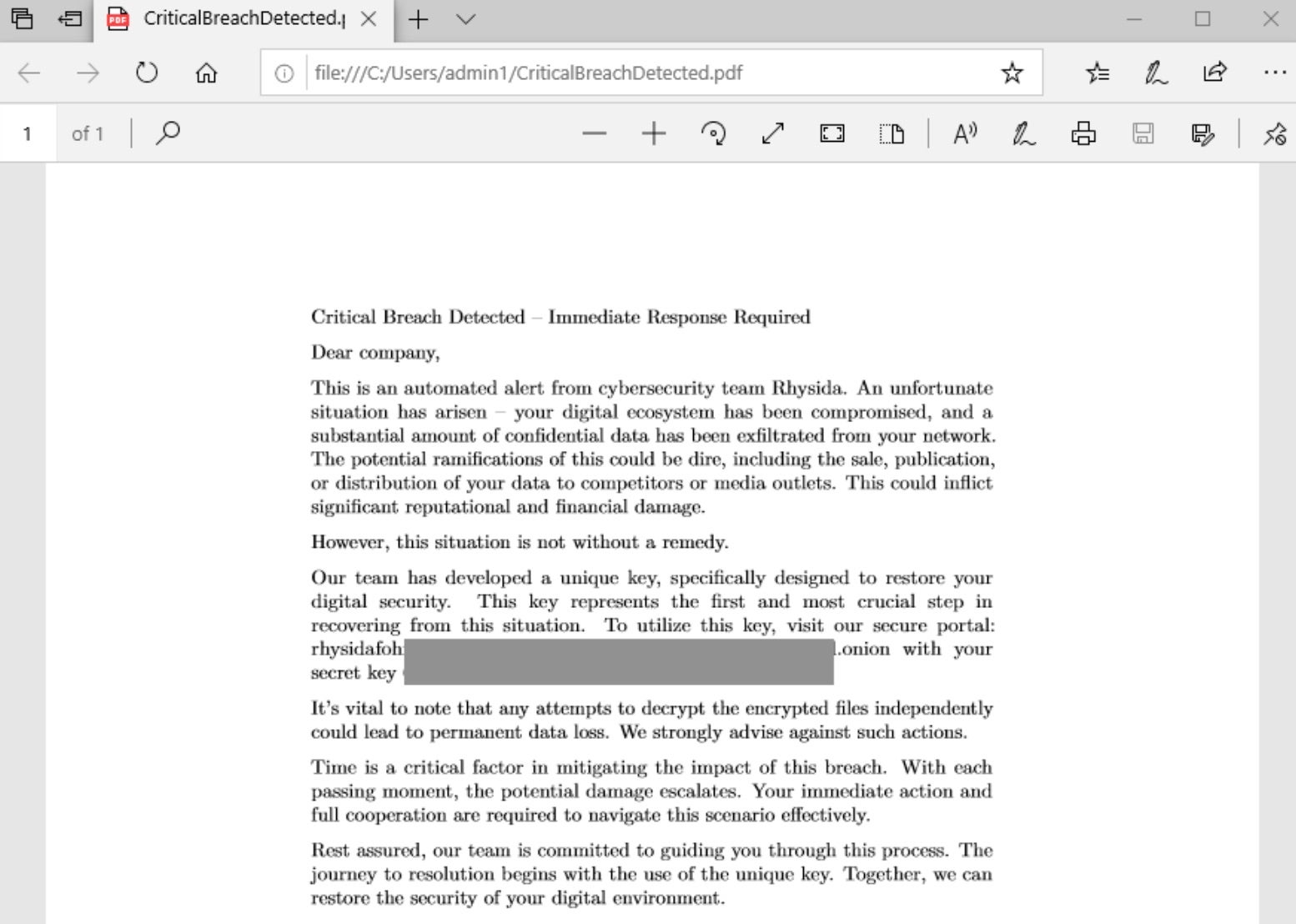
Rhysida - SentinelOne

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog

Malware Analysis Benefits Incident Response

The latest malicious activity and how to deal with it

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber
Interactive Online Malware Sandbox







