Malware analysis Malicious
Por um escritor misterioso
Descrição

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights
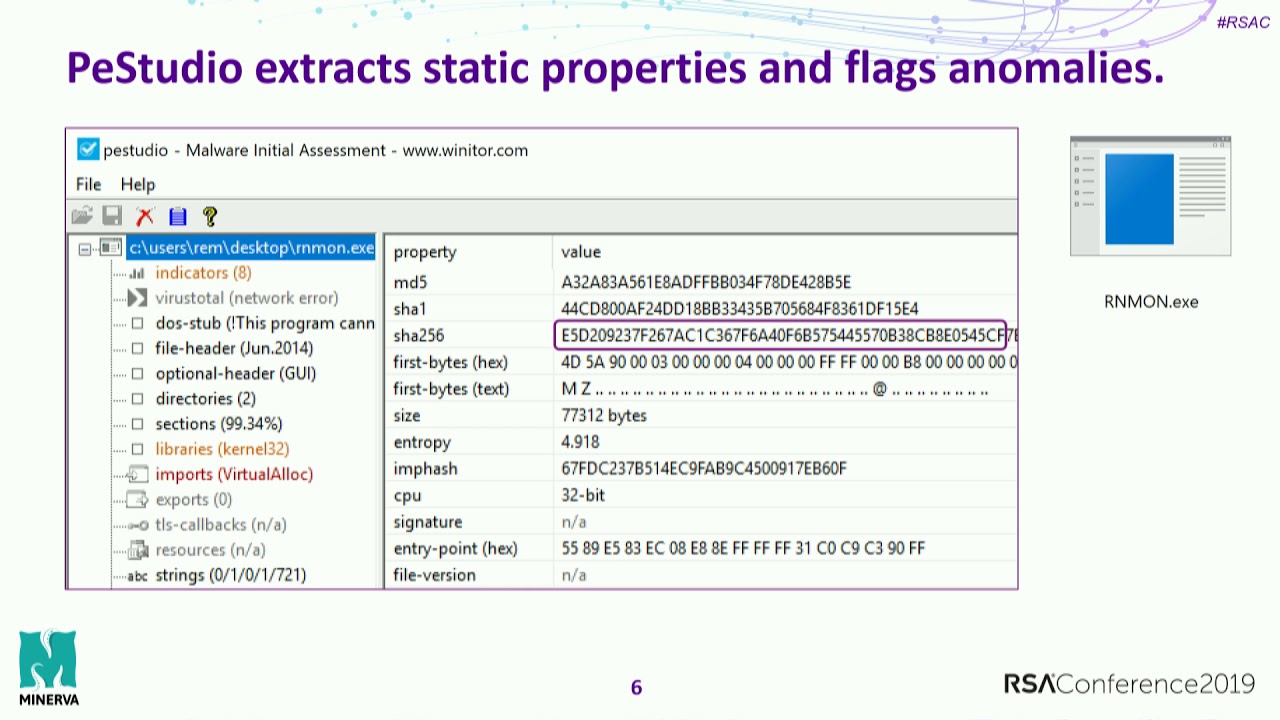
Practical Malware Analysis Essentials for Incident Responders

Malware Analysis Archives - zvelo

Malware Analysis: Steps & Examples - CrowdStrike

Practical Malware Analysis: Book review

A MS word malware analysis Part2: Analyzing malicious macros, by Nishan Maharjan

What Is Signature-Based Malware Detection? - Logix Consulting Managed IT Support Services Seattle

Introduction to Malware Analysis - PatchTheNet
Malware Analysis 4 Vital Stages of Malware Analysis You Should Know

Detecting and Analyzing Malware in the Kernel
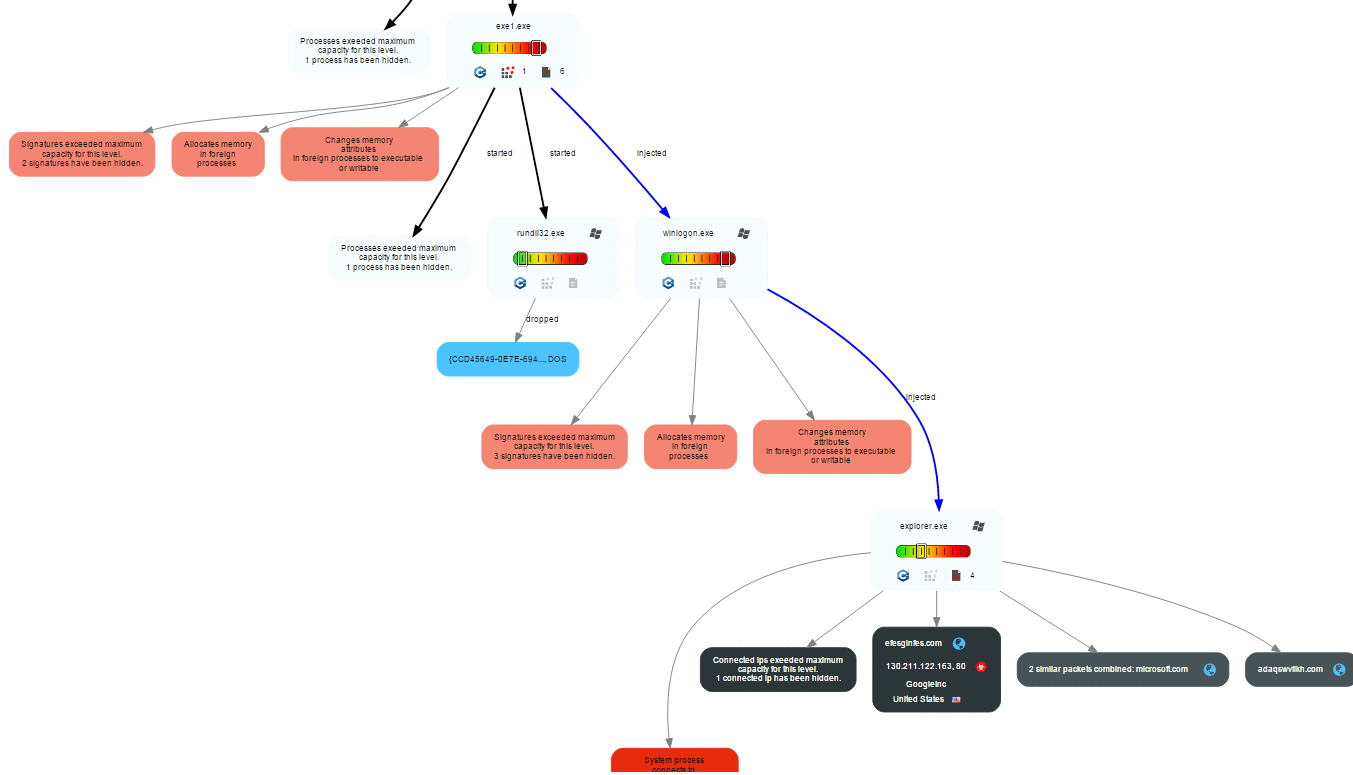
Deep Malware Analysis - Behavior Graph 2.0

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey

Malware Analysis - Malicious Doc

TryHackMe Malware Analysis







