Anti-Exfil: Stopping Key Exfiltration, by Blockstream, Blockstream Engineering Blog
Por um escritor misterioso
Descrição
In the wake of our recent launch of Blockstream Jade, we’d like to talk about a feature we’ve developed to eliminate the possibility of a certain hypothetical undetectable attack that a hardware…

Penetration Testing Active Directory, Part I

Keystone Wallet. Air-gapped. Open-source. Multisig. Offline
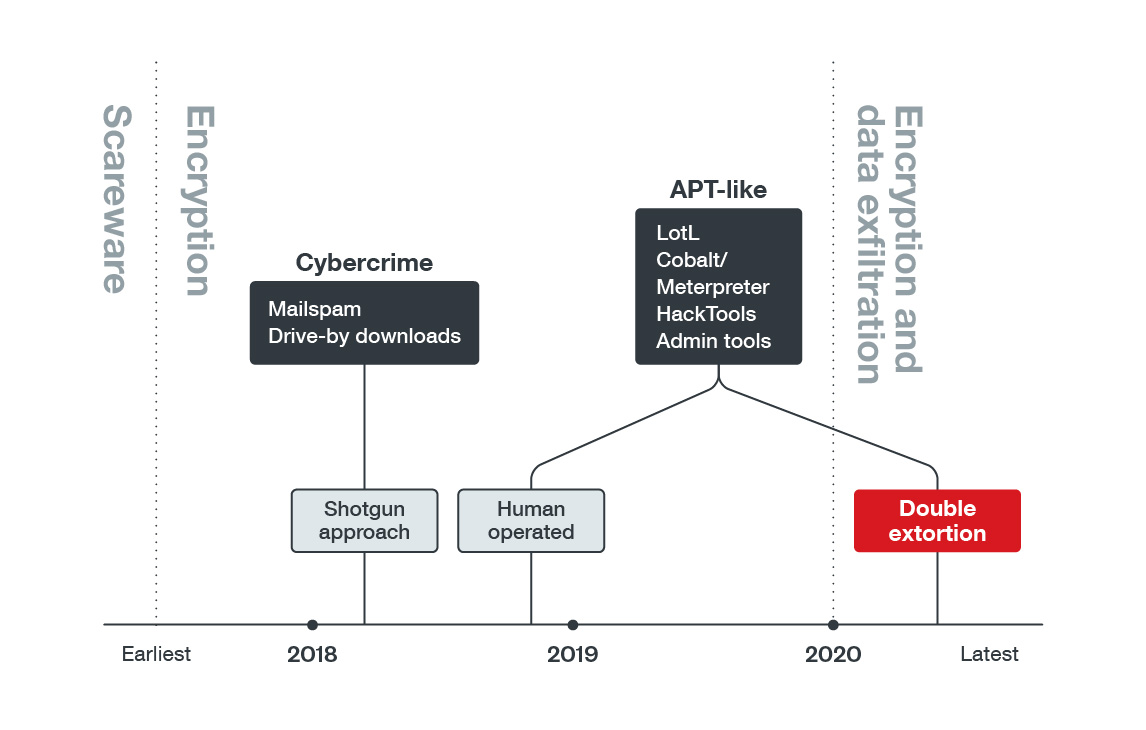
The State of Ransomware: 2020's Catch-22 - Security News - Trend
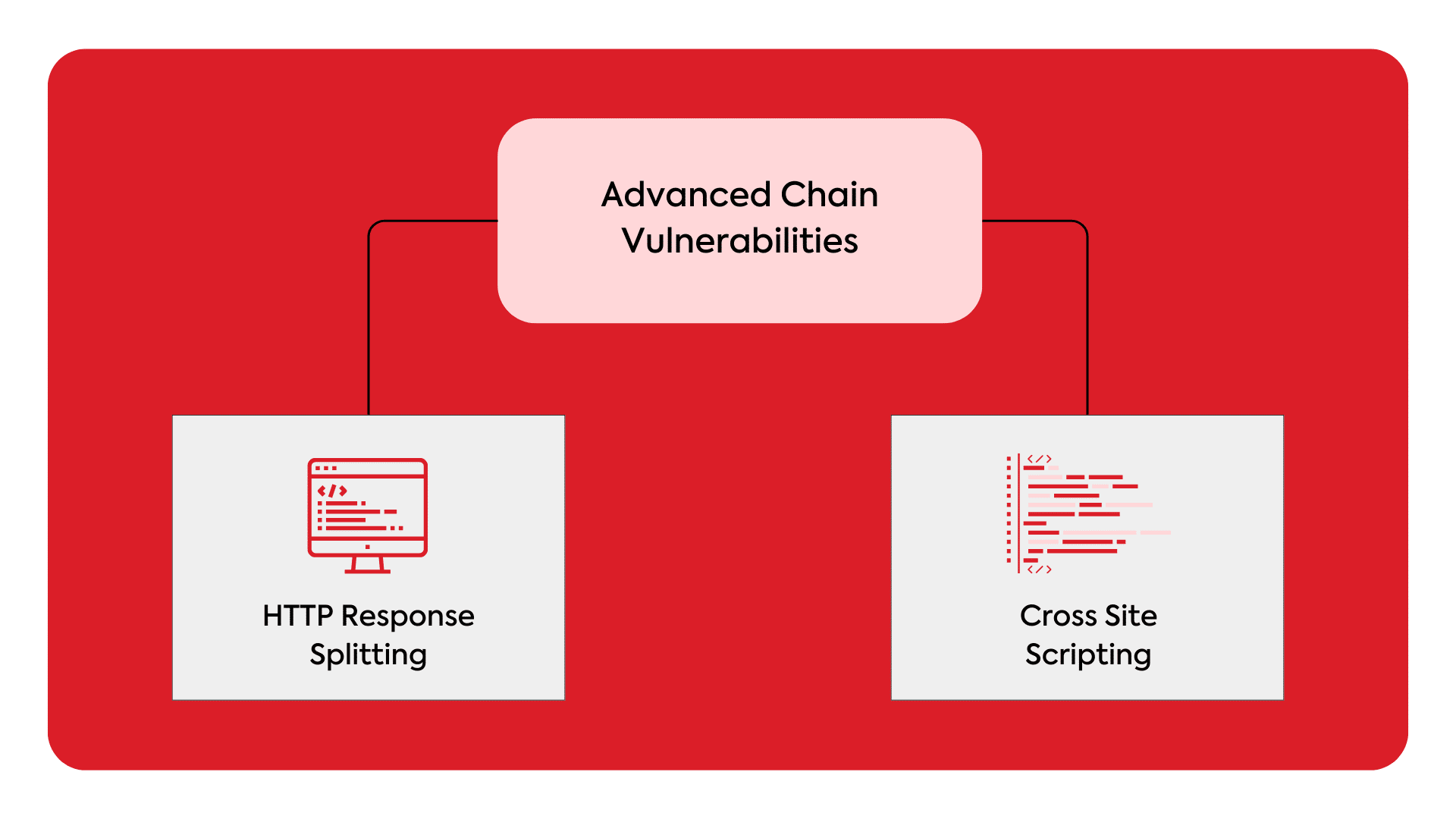
Understanding CRLF Injection: A Web App Vulnerability & Mitigation
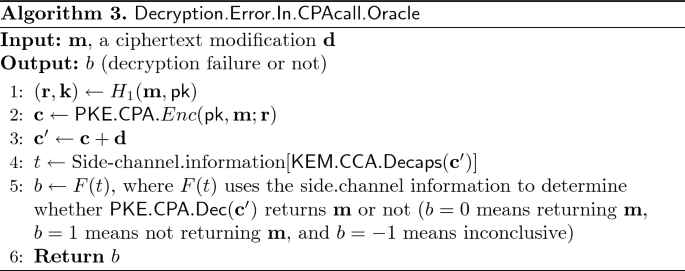
A Key-Recovery Timing Attack on Post-quantum Primitives Using the

HTTP Response Splitting Attack

Exploiting clickjacking vulnerability to trigger DOM based XSS
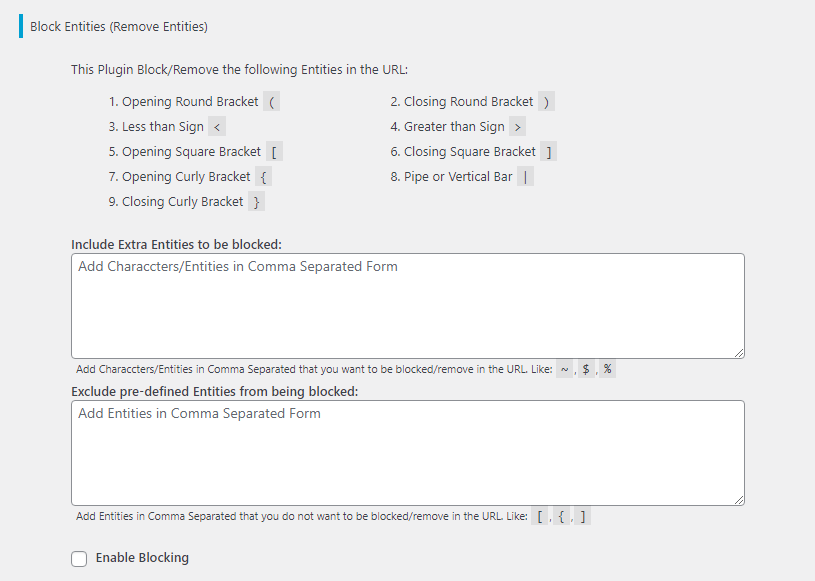
WordPress and Cross-Site Scripting (XSS) - Pressidium Hosting

Stream Cipher vs Block Cipher - Differences and Examples





