New ESXiArgs ransomware variant can evade CISA's recovery script
Por um escritor misterioso
Descrição
The cybercriminals behind the ESXiArgs ransomware have created a new variant that evades the recovery script that the U.S. CISA recently released. The new version also comes with a new ransom note.
ESXiArgs Ransomware: never too early to jump the gun

ESXiArgs Ransomware (2023) - How to recover a VM with no snapshots – Kevin Maschke

Cyber4Dev weekly update

ESXi Ransomware Update Outfoxes CISA Recovery Script
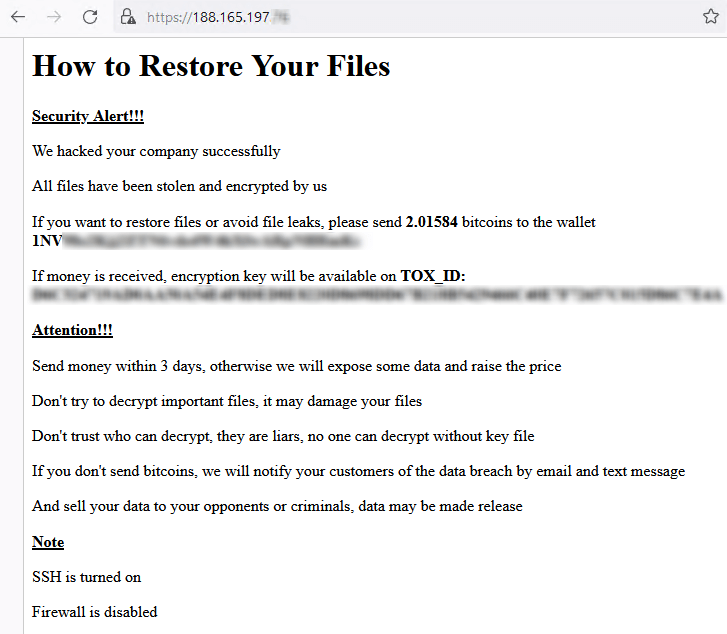
ESXiArgs: The new ransomware strain taking the world by storm

Undetected Mac Malware Spreading Via Pirated Apple Software - Spiceworks

New ESXiArgs ransomware variant can evade CISA's recovery script - Neowin
ESXiArgs Ransomware Virtual Machine Recovery Guidance
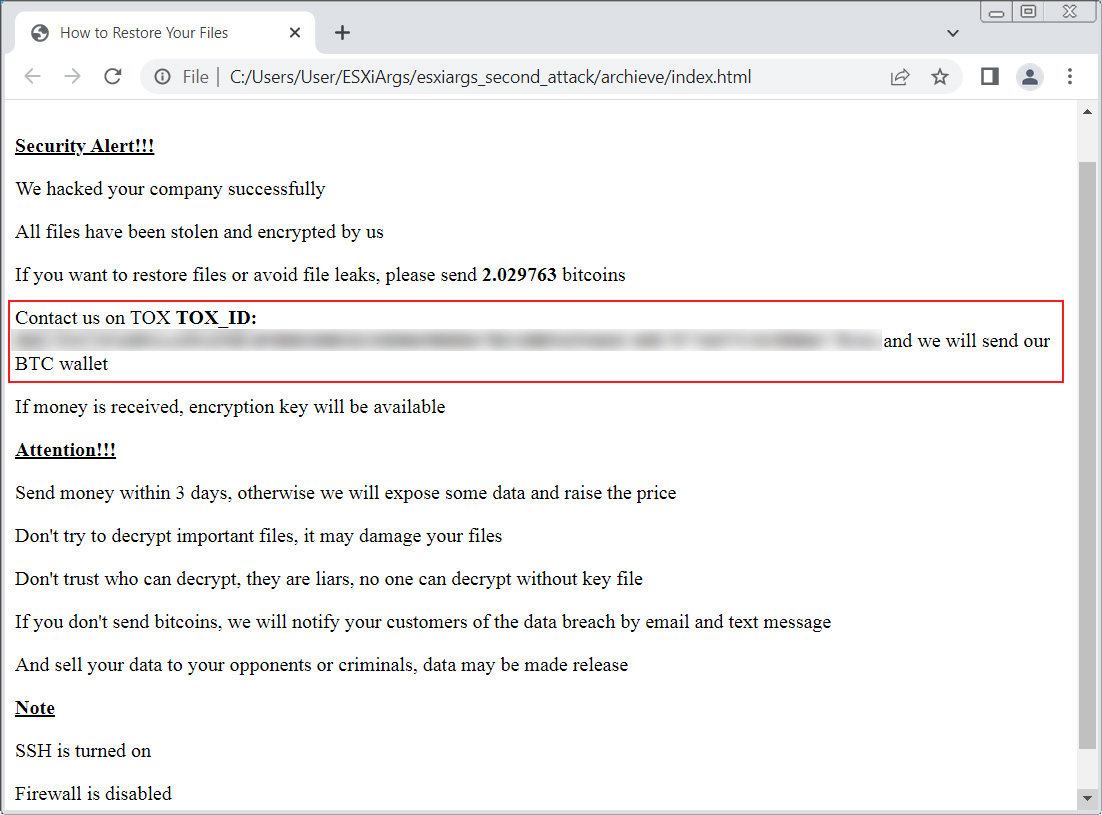
New ESXiArgs ransomware version prevents VMware ESXi recovery

ESXiArgs Ransomware Virtual Machine Recovery Guidance
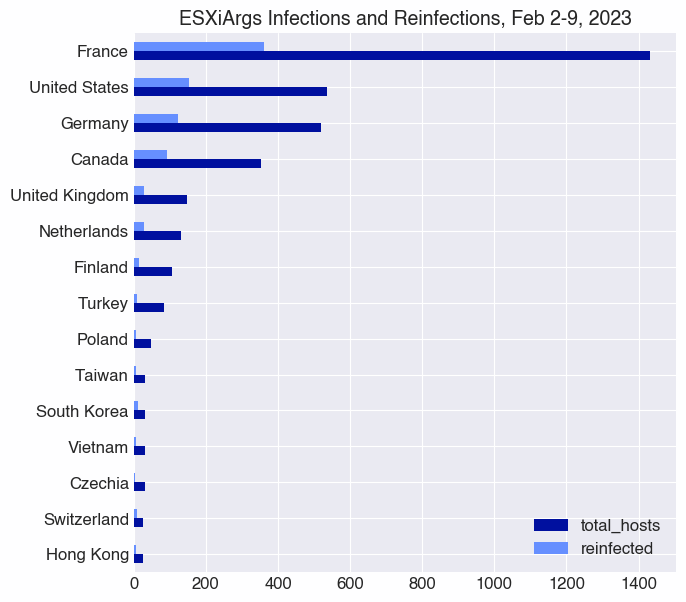
SOC Goulash: Weekend Wrap-Up - Opalsec
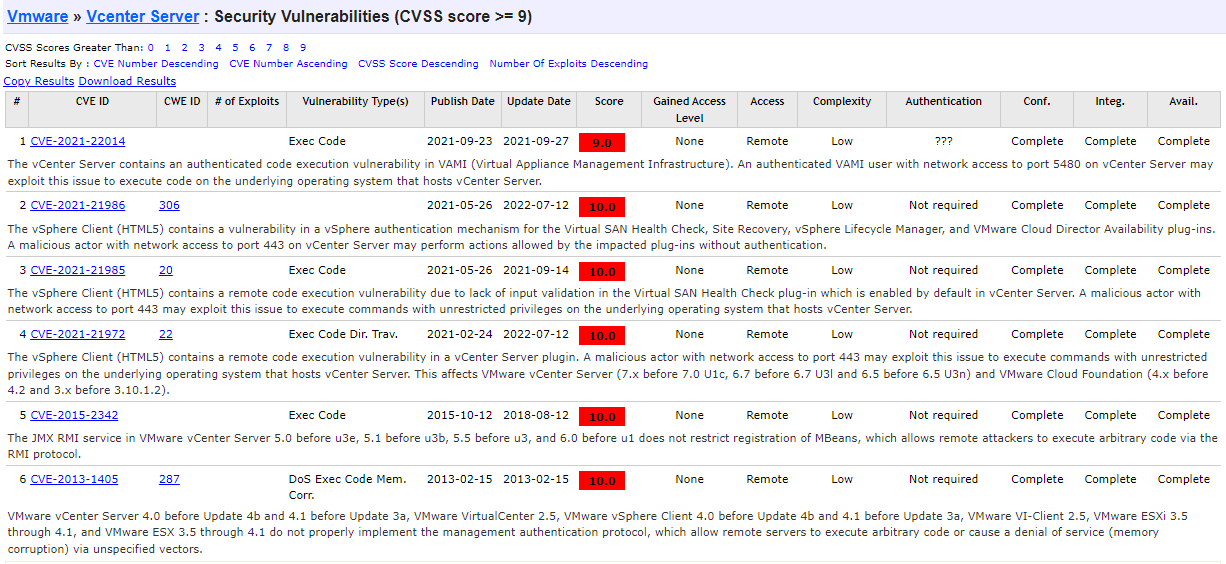
No Surprise! ESXiArgs Ransomware Attacks Exploit 2-Year-Old Vulnerability - All About Security

ESXWhy: A Look at ESXiArgs Ransomware - Censys

Ransomware notes: LockBit, Cl0p, and ESXiArgs. Vulnerability in automaker's management system. Russian cyberespionage.

Newsroom