Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Descrição
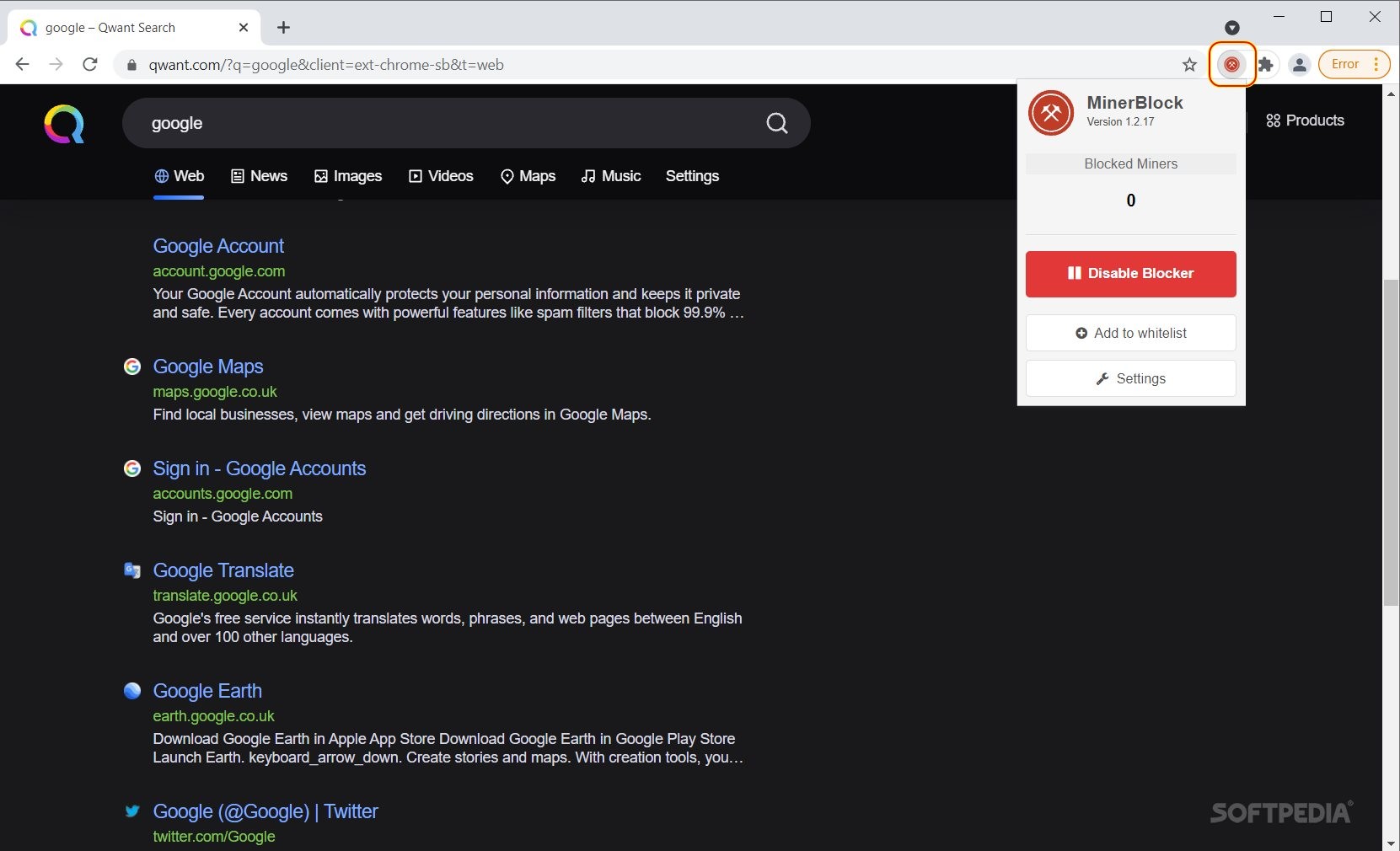
The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs
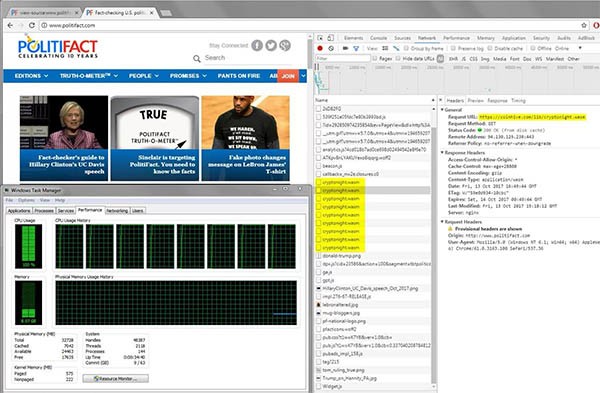
How Hackers Use Cryptojacking Malware to Take Over Computers to

PacNOG 23: Introduction to Crypto Jacking

ENISA Threat Landscape 2020 - Cryptojacking — ENISA
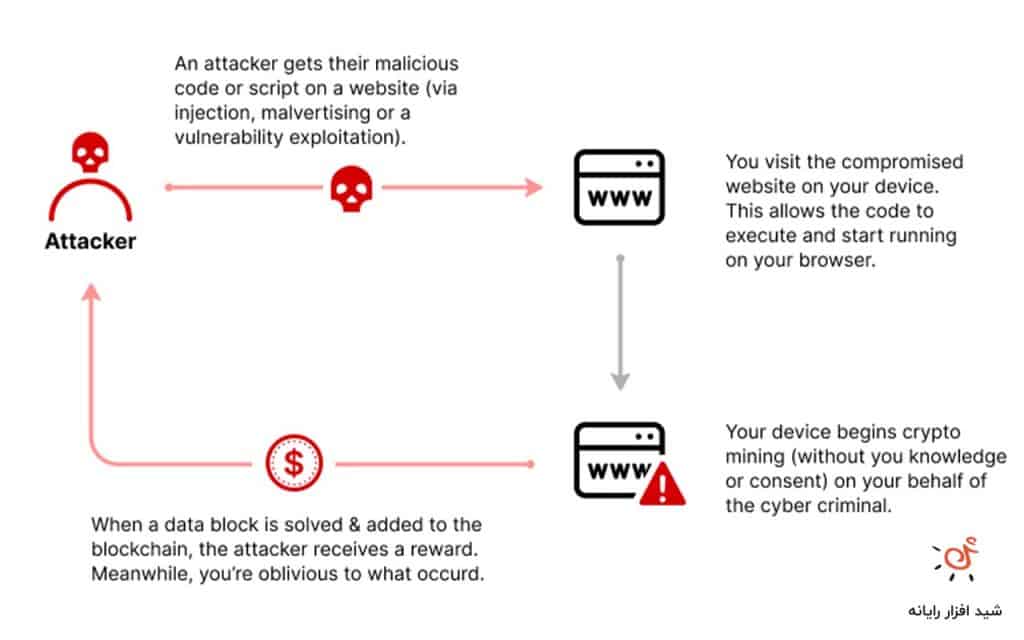
کریپتوجکینگ چیست؟ و چگونه میتوان از وقوع آن جلوگیری کرد؟

What is cryptojacking and how can you be affected? - alfa.cash blog
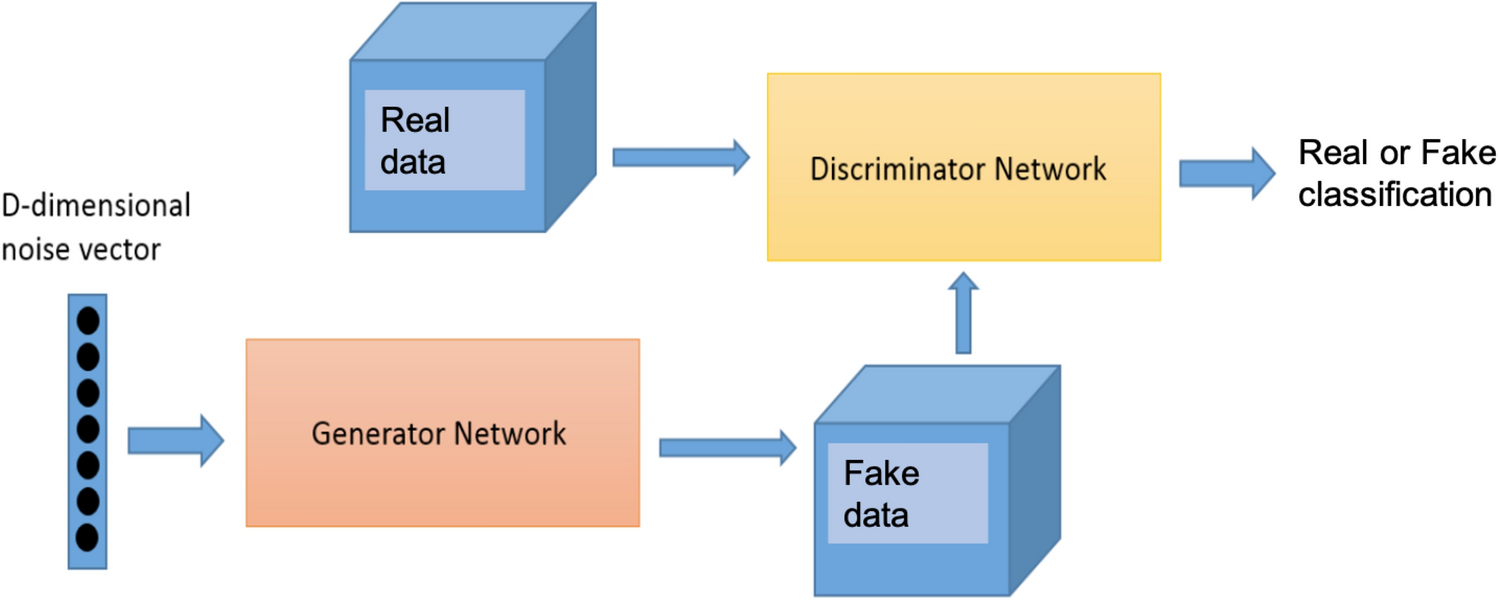
Synthetic flow-based cryptomining attack generation through

Cybersecurity Briefing A Recap of Cybersecurity News in
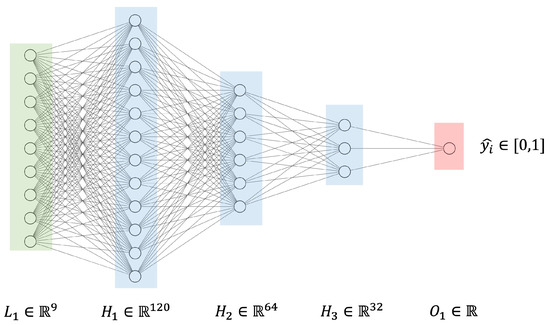
Applied Sciences, Free Full-Text
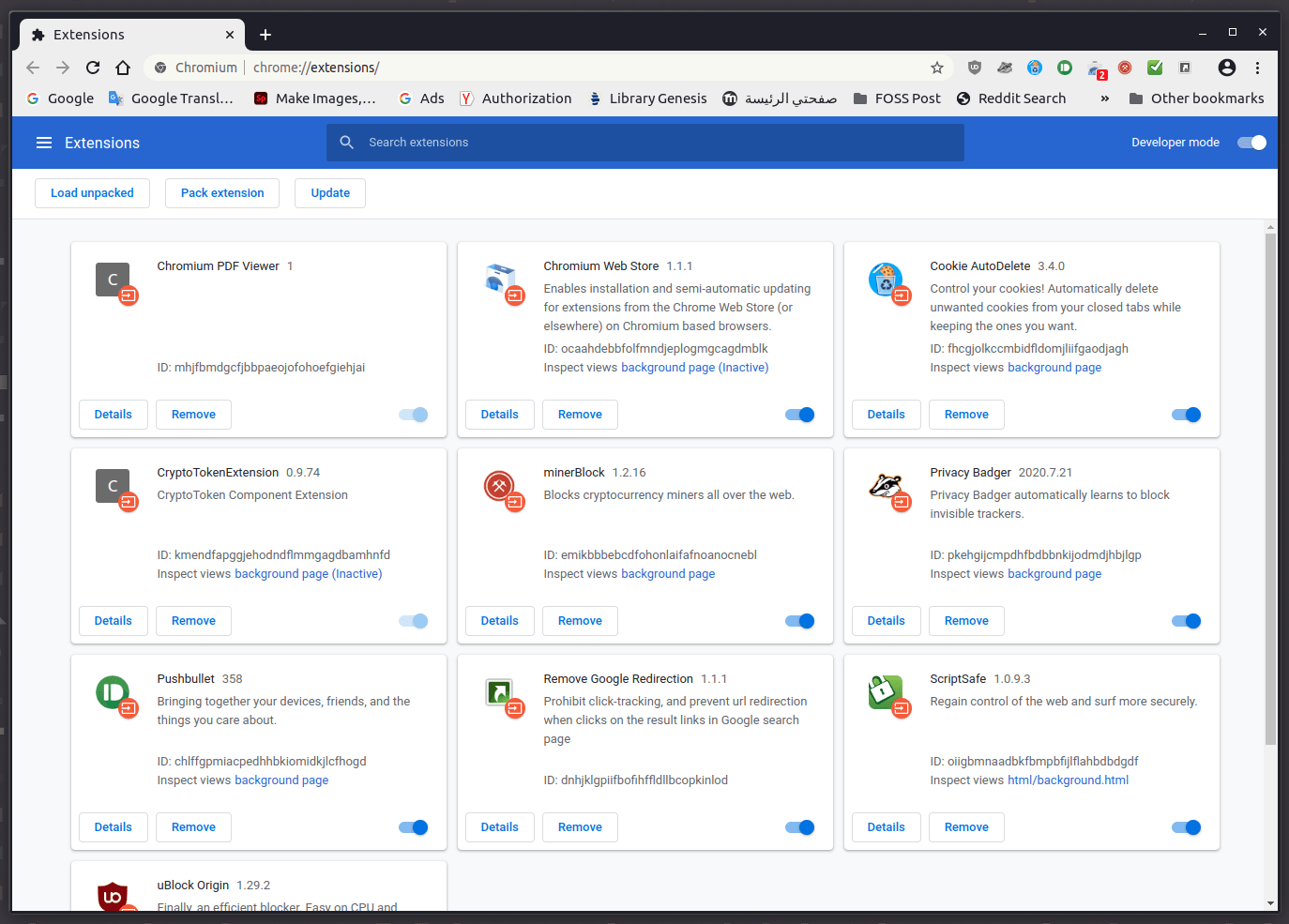
My device is being used for cryptojacking

ENISA's Threat Landscape and the Effect of Ransomware

Other 3,700 MikroTik Routers compromised in cryptoJacking campaigns
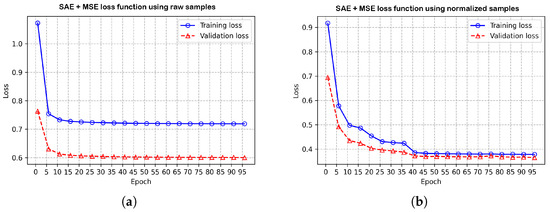
Applied Sciences, Free Full-Text