Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
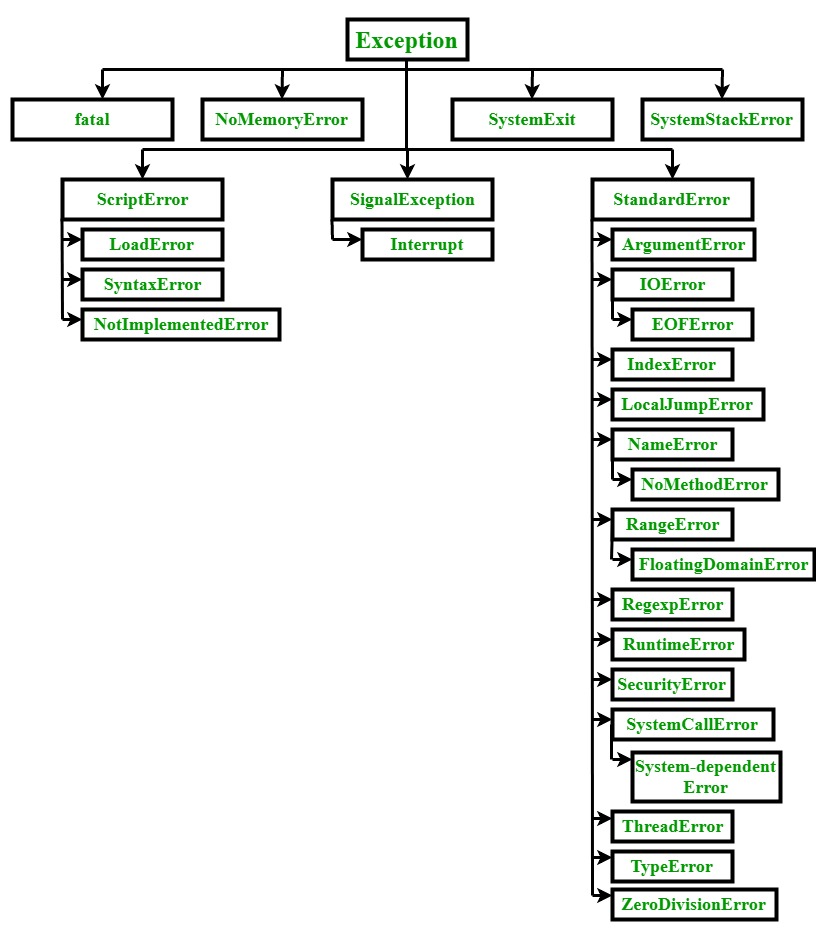
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

Secure Your AWS EC2 IMDS - Tenable Cloud Security

Why the C Programming Language Still Runs the World
Handle Exceptions - OutSystems 11 Documentation

Abusing Windows Internals - Part Two
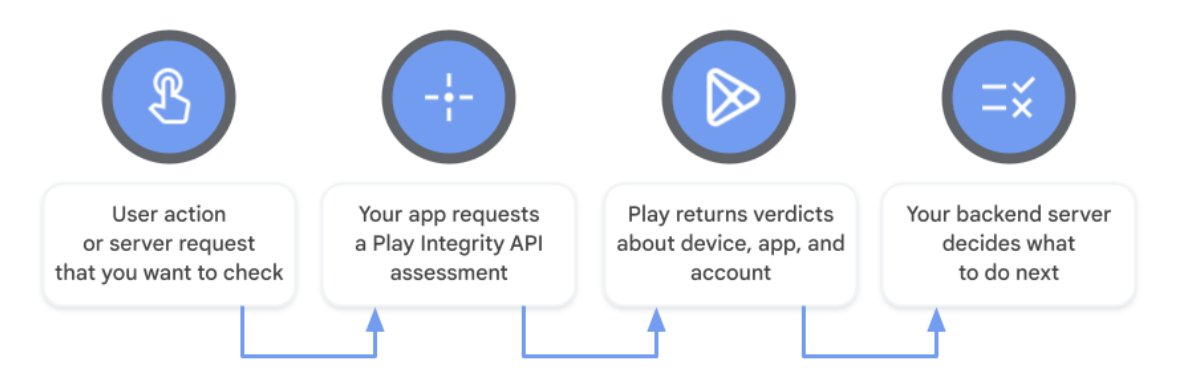
Overview of the Play Integrity API, Google Play
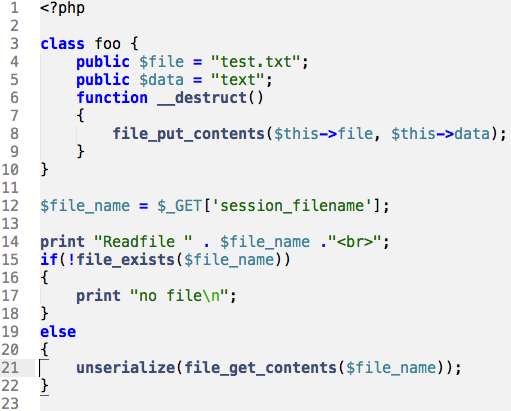
Remote code execution via PHP [Unserialize]
:max_bytes(150000):strip_icc()/ESOP_Final_4196964-2e25b96d22ce437497a38754c6c866ff.jpg)
Employee Stock Ownership Plan (ESOP): What It Is, How It Works

Code of Ethics for Government Services Poster

What is code injection?, Tutorial & examples

Microsoft Defender Attack Surface Reduction recommendations
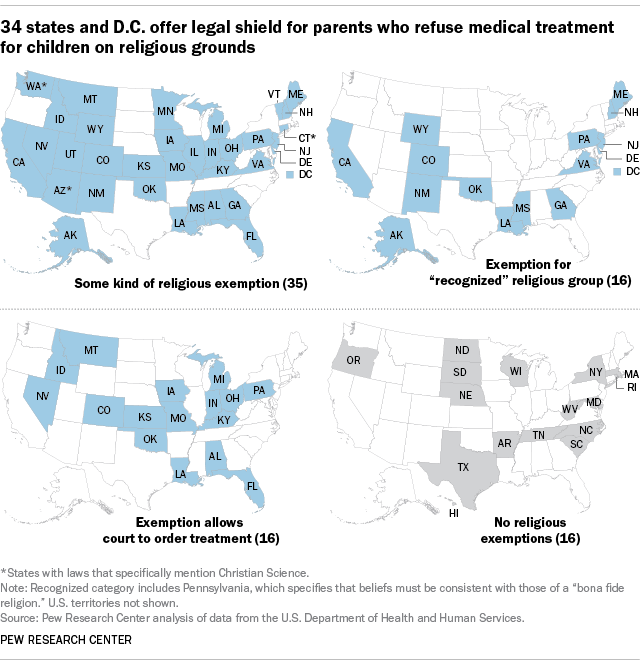
Most states' child abuse and neglect laws have religious

Exploiting OGNL Injection in Apache Struts